The world of computer security has plenty of confusing terms, though many of them are also very helpful to know so you can protect your data (and yourself). Here are a few:
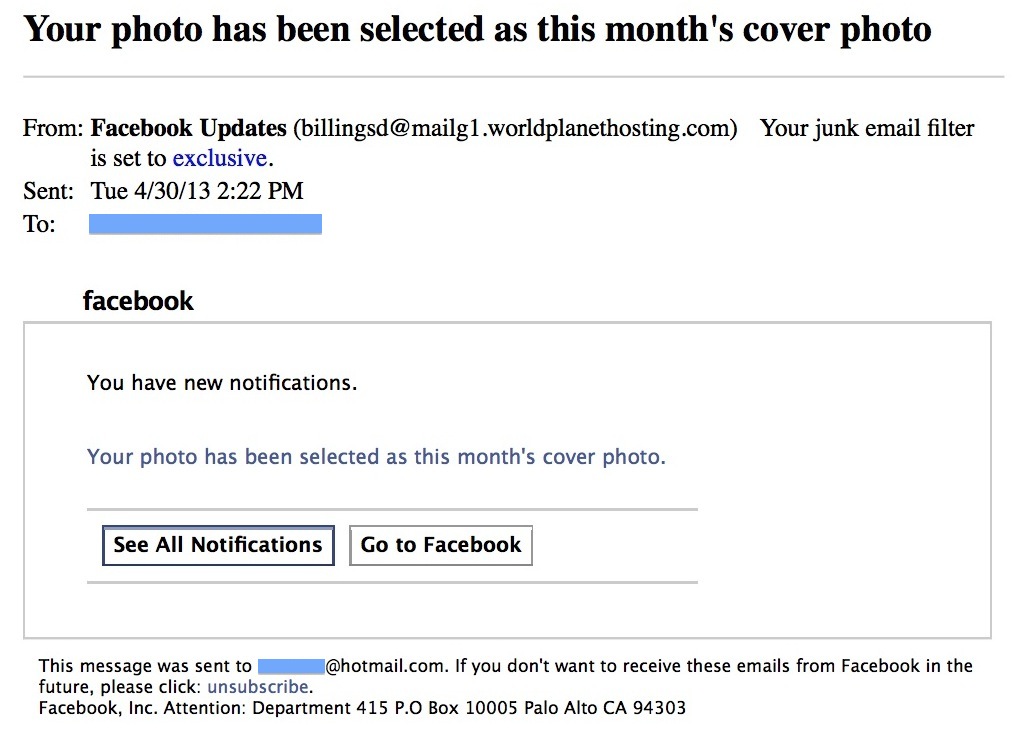
Drive-By Download: A drive-by download is a piece of malicious software (aka ‘malware’) that is downloaded onto your computer or mobile device without your knowledge when you visit an infected website. Although they are frequently found on malicious websites, drive-by downloads can also be lurking on normal ones that have been compromised by hackers. The best things you can do to defend yourself are to keep your software up-to-date (since malware often attacks through older security flaws that a given software manufacturer has already fixed via an update) and think before you click. If you’re using a desktop or laptop computer, you can hover over a given link before clicking on it. The destination address will appear on the lower left of your screen. If it’s something you don’t expect or haven’t seen before, don’t click on the link.
Jailbreaking: ‘Jailbreaking’ or ‘rooting’ a mobile device refers to overriding the manufacturer’s settings – including disabling the device’s security settings and future updates – to allow it to download and use apps and other features that are normally not enabled on the device (‘jailbreaking’ refers to the process as it applies to an Apple iPhone, iPod Touch or iPad and ‘rooting’ is much the same for a smartphone or tablet running the Android mobile operating system). The vast majority of mobile malware affects these devices since their security systems are badly compromised by the jailbreaking or rooting process and they should never be connected to a business computer network.
Read more ›