By Scott Aurnou
‘Phishing’ attacks are designed to steal your personal, financial and/or log in information. This can be done in a few ways, including via email or text message (referred to as ‘smishing’). They often contain links to websites that look legitimate but are really there to steal your account log in information or host malware ready to attack your computer as soon as you click on the link. These emails and messages can also be used to lure you into contact with scam artists posing as potential clients or officials offering to release substantial funds to you if only you would be so kind as to give them detailed personal information and/or a sum up front. Phishing attacks are generally designed to make you take action by either frightening or tempting you. Some of them are actually very well crafted. Some not so much. And some border on the ridiculous. Each month at The Security Advocate, we will present a few examples, along with explanations of what to look out for to avoid falling victim to one of the scams.
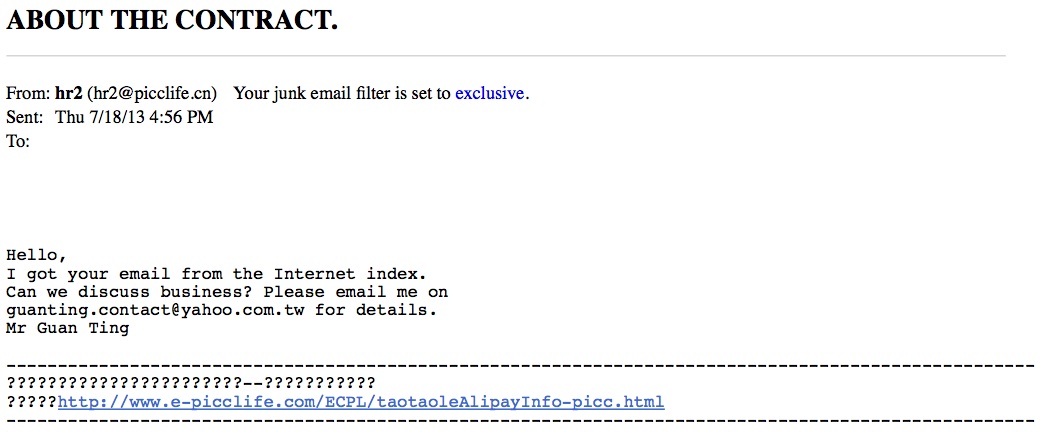
This email tries to grab your attention with the ominous-sounding all caps subject ABOUT THE CONTRACT and reads:
Hello,
I got your email from the Internet index.
Can we discuss business? Please email me on
guanting.contact@yahoo.com.tw for details.
Mr Guan Ting
While this particular message is a rather clumsy attempt to entice the recipient with the possibility of a business arrangement, much better versions of this sort of scam are not uncommon. They often (but not always) target lawyers and other professionals who can ‘help’ them collect an allegedly unpaid debt. The debt will appear to be settled without much trouble and the new client will be happy with the fine work. He or she will then instruct the email recipient to deduct their fee and send over the balance of the amount collected. After the funds have been sent out, of course, the debt payment will turn out to be bogus and the overseas ‘client’ will never be heard from again. This sort of scam is not new, and the ABA and a number of individual state bar associations have warned attorneys about them. If you receive an email like this, don’t respond to it. If anything, consider forwarding it to the U.S. Attorney’s Office or the F.B.I.
Read more ›














