By Scott Aurnou
‘Phishing’ attacks are designed to steal your personal, financial and/or log in information. This can be done in a few ways, including via email or text message (referred to as ‘smishing’). They often contain links to websites that look legitimate but are really there to steal your account log in information or host malware ready to attack your computer as soon as you click on the link. These emails and messages can also be used to lure you into contact with scam artists posing as potential clients or officials offering to release substantial funds to you if only you would be so kind as to give them detailed personal information and/or a sum up front. Phishing attacks are generally designed to make you take action by either frightening or tempting you. Some of them are actually very well crafted. Some not so much. And some border on the ridiculous. Each month at The Security Advocate, we will present a few examples, along with explanations of what to look out for to avoid falling victim to one of the scams.
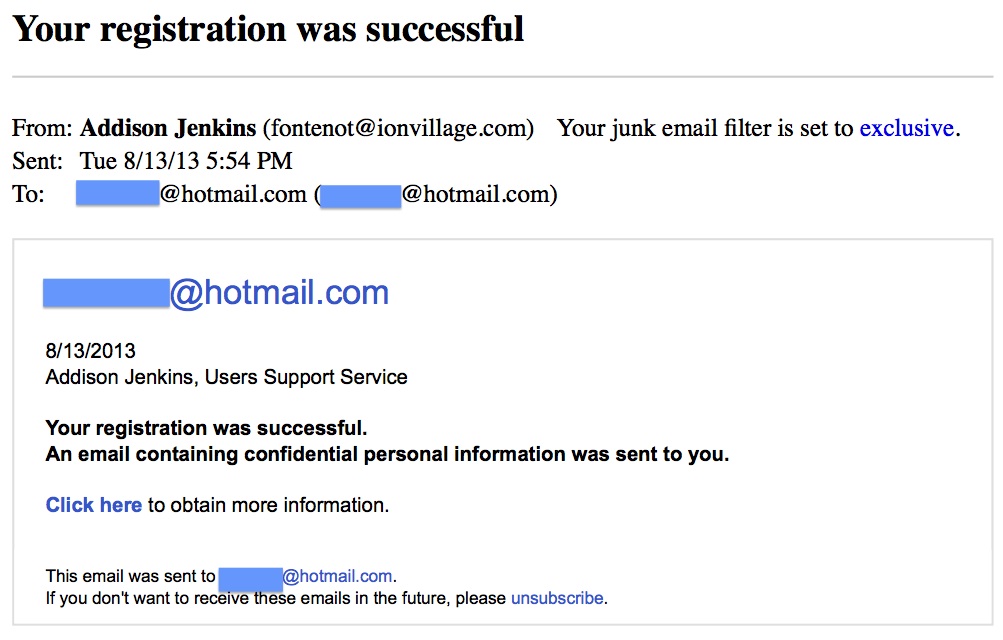 First up, we have a confirmation message for something you don’t recall signing up for. The subject line is “Your registration was successful” and it reads as follows:
First up, we have a confirmation message for something you don’t recall signing up for. The subject line is “Your registration was successful” and it reads as follows:
Addison Jenkins, Users Support Service
Your registration was successful.
An email containing confidential personal information was sent to you.
Click here to obtain more information.
The idea here is simple: you receive the email, wonder what service sent it (as that information is conspicuously absent), click on the link, and your computer will be immediately attacked by malware and/or you will be take to a website with a form you can fill out (with account and/or detailed personal information) to ‘opt out’ of the service you never signed up for. This will give the scammers who actually sent the message enough data to break into your online accounts and possibly impersonate you, as well. Any message like this is a fake. Simply put: you should never click on any links contained in an email (or text message) coming from someone you don’t know.
Read more ›














