By Scott Aurnou
‘Phishing’ attacks are designed to steal your personal, financial and/or log in information. This can be done in a few ways, including via email or text message (referred to as ‘smishing’). They often contain links to websites that look legitimate but are really there to steal your account log in information or host malware ready to attack your computer as soon as you click on the link. These emails and messages can also be used to lure you into contact with scam artists posing as potential clients or officials offering to release substantial funds to you if only you would be so kind as to give them detailed personal information and/or a sum up front. Phishing attacks are generally designed to get you to take action by either frightening or tempting you. Some of them are actually very well crafted. Some not so much. And some border on the ridiculous. Each month at The Security Advocate, we will present a few examples, along with explanations of what to look out for to avoid falling victim to one of the scams.
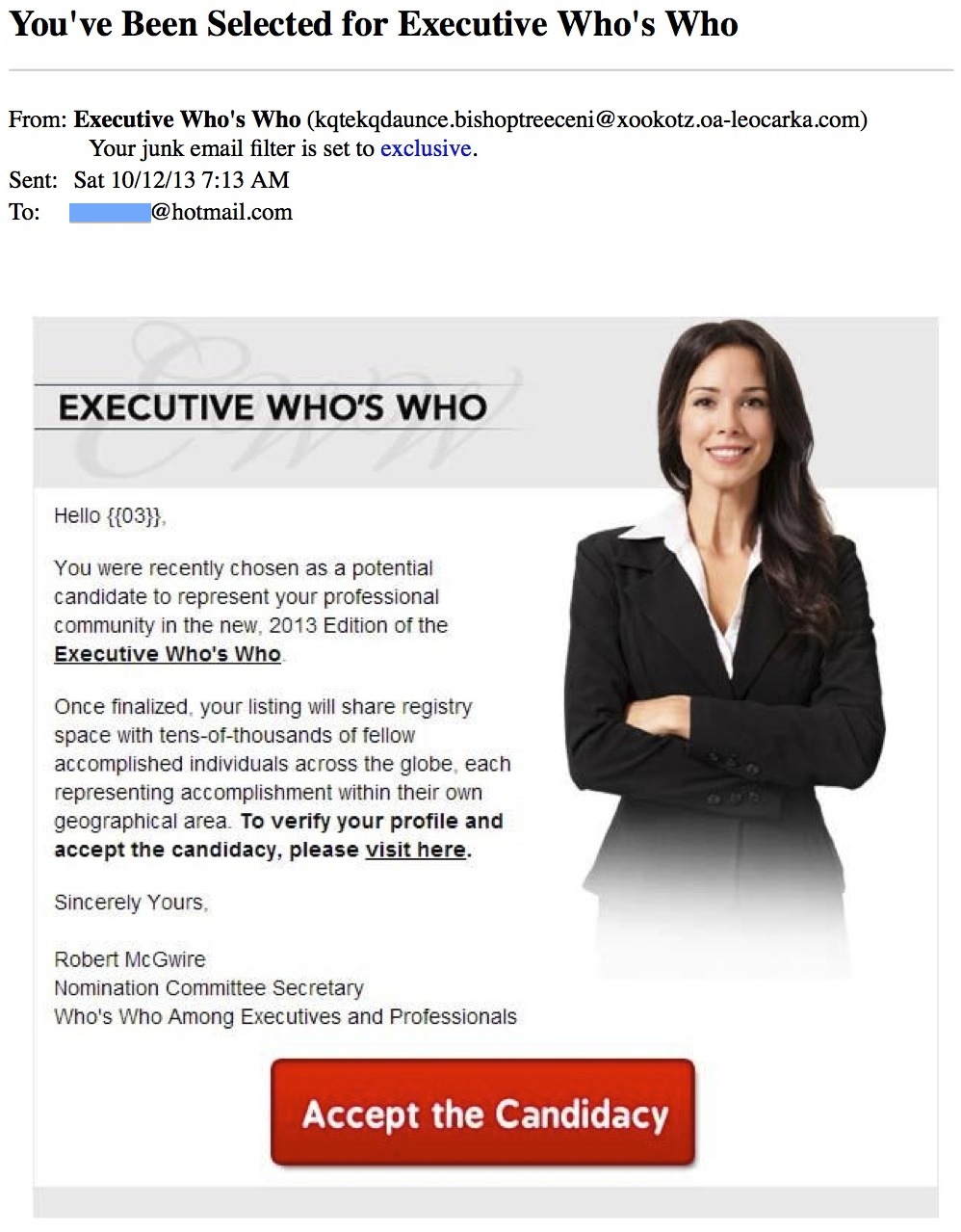
First up, we have a message with the subject line: “You’ve Been Selected for Executive Who’s Who.” Sounds exciting, except that the impressive-sounding list is a fictional one. Moreover, the message is actually just the image above – and that’s not even text, just a picture of it. The pictured text reads:
Hello {{03}},
You were recently chosen as a potential candidate to represent your professional community in the new, 2013 Edition of Executive Who’s Who.
Once finalized, your listing will share registry space with tens-of-thousands of fellow accomplished individuals across the globe, each representing accomplishment within their own geographical area. To verify your profile and accept the candidacy, please visit here.
Sincerely Yours,
Robert McGwire
Nomination Committee Secretary
Who’s Who Among Executives and Professionals
The message asks you to verify a profile that you haven’t created in the first place. If you click on any part of the image, your computer will be hit with malware and/or you will be invited fill out a form with personal (and likely financial) details to “accept the candidacy.” Also, notice the mismatched sender’s name and email address. This generally indicates an automated message sent via a botnet solely to attack the recipient of the message. The vast majority of spam emails come from computers under the command of a botnet. Of course, your best move is to just delete it.
Read more ›













