By Scott Aurnou
‘Phishing’ attacks are designed to steal your personal, financial and/or log in information. This can be done in a few ways, including via email or text message (referred to as ‘smishing’). They often contain links to websites that look legitimate but are really there to steal your account log in information or host malware ready to attack your computer as soon as you click on the link. These emails and messages can also be used to lure you into contact with scam artists posing as potential clients or officials offering to release substantial funds to you if only you would be so kind as to give them detailed personal information and/or a sum up front. Phishing attacks are generally designed to get you to take action by either frightening or tempting you. Some of them are actually very well crafted. Some not so much. And some border on the ridiculous. Here are a couple of examples, along with explanations of what to look out for to avoid falling victim to one of the scams.
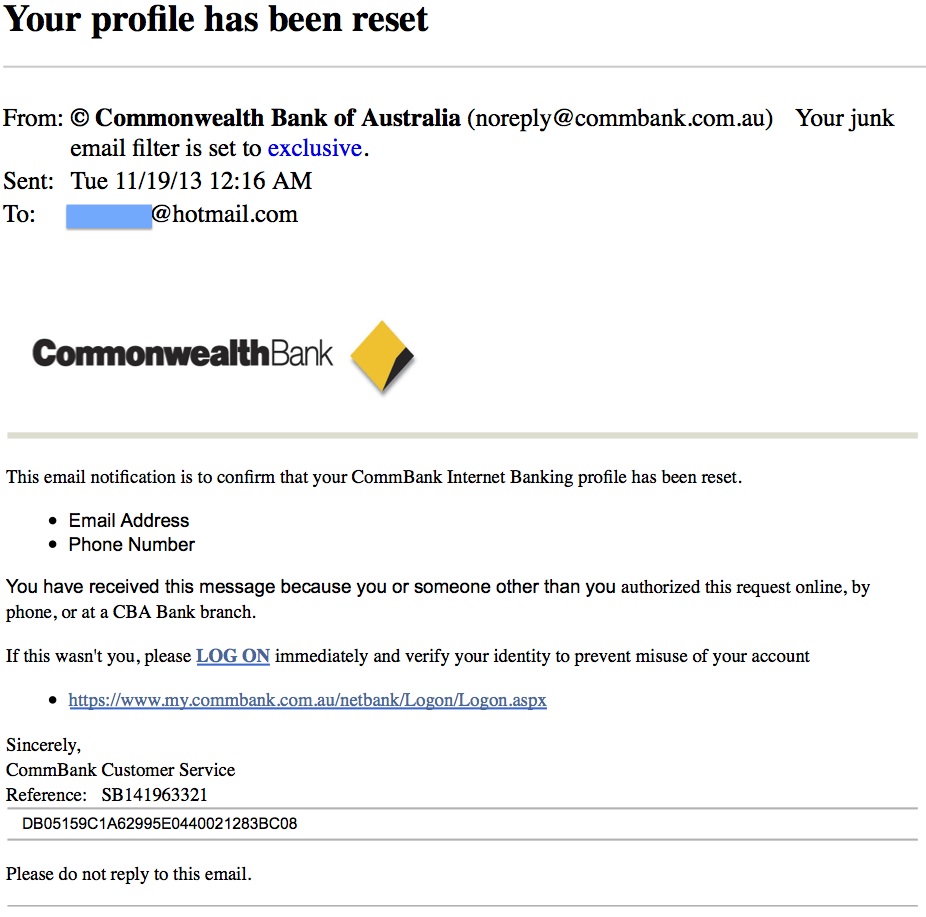
This message purports to come from ‘Commonwealth Bank of Australia’ and reads:
This email notification is to confirm that your CommBank Internet Banking profile has been reset.
Email Address
Phone Number
You have received this message because you or someone other than you authorized this request online, by phone, or at a CBA Bank branch.
If this wasn’t you, please LOG ON immediately and verify your identity to prevent misuse of your account
https://www.my.commbank.com.au/netbank/Logon/Logon.aspx
Sincerely,
CommBank Customer Service Reference: SB141963321
DB05159C1A62995E0440021283BC08
Please do not reply to this email.
While you should always be very suspicious of any unsolicited email appearing to come from a bank, this one is a fairly well-designed phishing attack. It includes an accurate-looking bank logo and is relatively well-written. It’s still fake, though. The threat of a locked account is a fairly typical one used by scam artists and is intended to scare you into immediate action. Invariably, you can ‘reauthorize’ your account if you just give the sender your personal and/or log in information. Never do this. The threat is fake. The message does not come from the actual Commonwealth Bank, your account is not locked and ‘reauthorizing’ it is simply giving your information to cyber criminals. Another thing that can make this phishing email appear convincing is that it appears to come from a “noreply@commbank.com.au” email address, which looks legitimate. Unfortunately, a sender’s name and/or email address can be faked through a process known as ‘spoofing.’
If you do see an email like this, don’t think twice and don’t respond to it or click on any links in the message. Just delete it. If you are at all concerned when you receive one, contact the bank directly, using the telephone number on the back of your bank card or on one of your bank statements. You can also go directly to the bank’s website to check. Just be sure you don’t call any number or click on any link in the email itself.
Read more ›














